Data Security, Powered by Coro
Comprehensive Cybersecurity, Simplified
Coro data security and endpoint protection solutions fit perfectly with Adaptiv Networks’ multi-layered network security, offering you added peace of mind that comes with a comprehensive cybersecurity strategy.

Why Coro?
Adaptiv SD-WAN and SASE solutions protect against threats moving through your network, but what about threats that are lurking in data that’s stored in your cloud servers, emails or employee devices?
Coro adds protection for data and endpoints that complements Adaptiv’s network security to create a comprehensive cybersecurity posture. With no complicated integrations, and no technical challenges, Coro solutions are ideal for SMEs with lean IT teams. Simply choose a Coro cybersecurity suite that fits your business, or Coro Complete for total protection.
How Coro Simplifies Data Security and Endpoint Protection
Building a cybersecurity stack has always meant buying multiple, segmented tools from multiple vendors, training employees on each one, and dealing with multiple interfaces and endpoint agents. Until now. Coro is one platform with many modules. Get all the security you need now, with the ability to switch on any module you need in the future.
One Interface
All modules feed into one, easy-to-use dashboard, in which you can quickly view and even respond to statuses, events, and logs.
One Endpoint Agent
Device posture, NGAV, EDR, VPN, firewall, and data governance on one easy-to-manage endpoint agent, eliminating agent conflicts.
One Data Engine
Modules inform each other through a shared data engine, eliminating the need for integration and improving security posture.
Coro cybersecurity suites tailored to fit your business needs

Get essential coverage for endpoints, email, and cloud apps, automating resolution of most security incidents.
Included modules
- Endpoint Security
- Endpoint Detection & Response (EDR)
- Email Security
- Cloud App Security
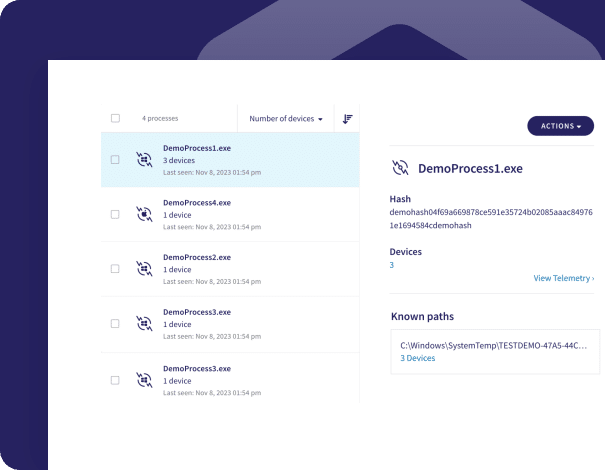
Log all endpoint activity, analyze data anomalies, and automate resolution of 95% of security incidents.
Included modules
- Endpoint Security
- Endpoint Data Governance
- Endpoint Detection & Response (EDR)
- WiFi Phishing
Scan emails for threats and remediate them automatically, drastically cutting the time needed to manage email security.
Included modules
- Email Security
- User Data Governance
- Secure Messaging Encryption
- Inbound Gateway
Explore Coro Cybersecurity Modules
Coro modules are self-contained security components that can be turned on or off within the Coro platform. Each module performs as well as, or better than, legacy solutions in its security domain. Our Coro bundles combine multiple modules into affordable cybersecurity solutions.
Endpoint Security is the core endpoint module in Coro.
Capabilities:
- Device Posture: Apply policies to users or groups and determine the remediation action for vulnerabilities.
- Next-gen Antivirus: Advanced threat protection (ATP) analyzes both static files and running processes for anomalies.
- Allow/Block Lists: Create lists of files, folders, and processes to allow or block on your protected endpoints.
The Endpoint Detection and Response (EDR) module extends your ability to handle incidents as they occur. You can remediate quickly to prevent further damage from known and unknown threat sources and to conduct post-breach analysis.
It continuously monitors endpoint devices and presents these findings in clear, easy-to-manage tabs from the Coro dashboard. Filter through the data as needed, and receive remediation guidance and immediate response actions.
Capabilities:
- Enhanced malicious software detection
- Proactive isolation of infected devices
- Automatic remediation across endpoints
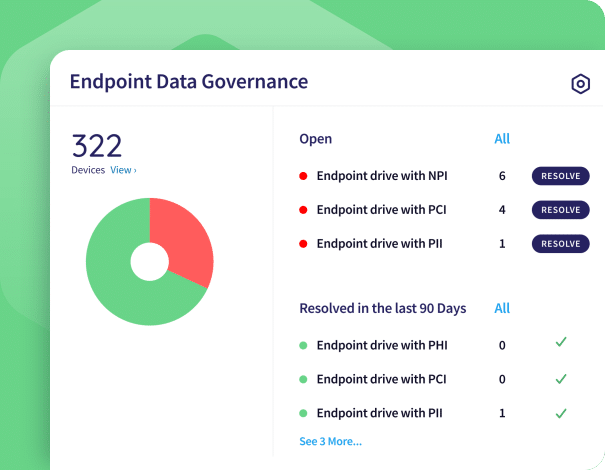
The Endpoint Data Governance module protects sensitive data from unauthorized access, use, disclosure, modification, or destruction across endpoints.
To help ensure compliance with these regulatory standards, Coro lets you remotely scan endpoints for:
- PII (personally identifiable information)
- PHI (protected health information)
- PCI (payment card information)
- NPI (non-public information)
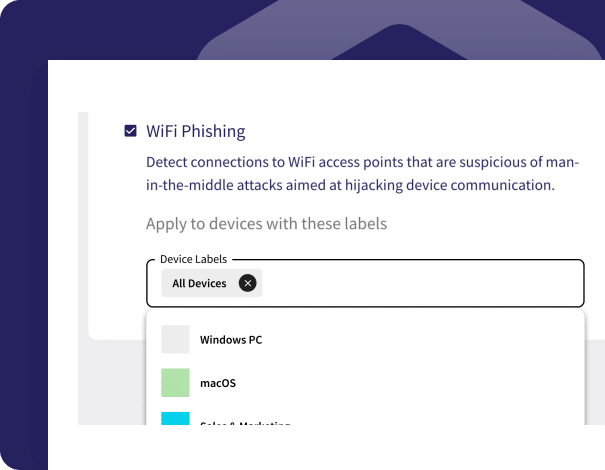
The WiFi Phishing add-on guards endpoints outside the LAN (local area network) by preventing connections to suspicious WiFi access points. It works by detecting connections to WiFi access points that are suspicious of man-in-the-middle attacks aimed at hijacking device communication.
Protects:
- All devices in your workspace
- Specific groups of devices
- Remote/ traveling employees
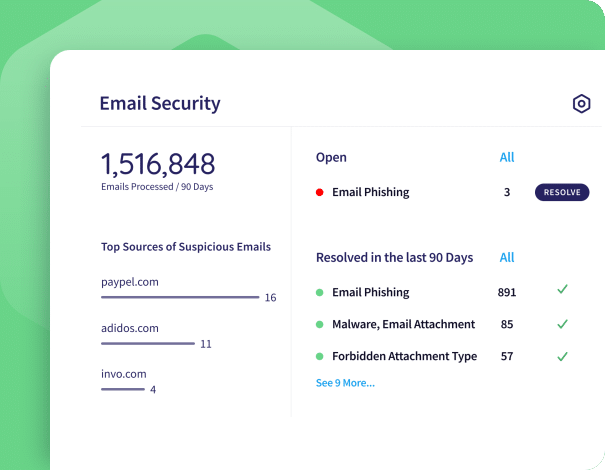
Email Security is the core email module in Coro.
Capabilities:
- Malware Scanning: Identify and quarantine emails with potential malware or ransomware attachments.
- Email Phishing Protection: Prevent threats from domain impersonation, spoofing, and other misleading phishing attempts.
- Allow/Block Lists: Create and maintain a list of individual senders or sending domains to allow or block from your business inboxes.
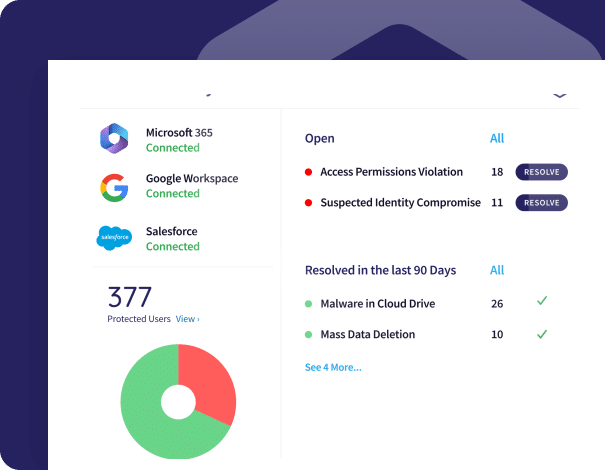
Cloud Security is one of the core SASE modules in Coro.
With it, you can stop abnormal admin activity, access violations, ID compromise, malware, and mass data changes in the following cloud apps: Microsoft Office 365, Google Workspace, Slack, Dropbox, Box, and Salesforce.
Blocks:
- Abnormal admin activity
- Malware in cloud drive
- Suspected identity compromise
- Access permissions violation
- Suspected bot attacks
- Mass download
- Mass deletion
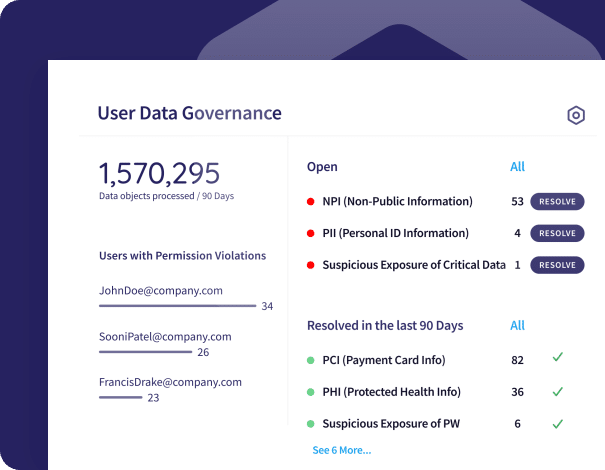
The User Data Governance module helps administrators establish a data handling strategy. Make sure data is only being accessed by by authorized users and maintain compliance to strict regulatory standards.
This module scans emails for unauthorized disclosure of sensitive sensitive data like:
- PII (personally identifiable information)
- PHI (protected health information)
- PCI (payment card information)
- NPI (non-public information)
- Passwords
- Source code
- Certificates
- Custom keywords
The Secure Messages add-on lets you encrypt outbound emails. With this module, you can use a private key to ensure only the intended recipients to access emails.
Works with:
- Microsoft O365
- Google Workspaces
- Desktop email
- Mobile email apps

The Inbound Gateway add-on is a proxy that provides real-time detection and protection for incoming emails. It lets you intercept inbound emails and inspect them, allowing only threat-free or trusted emails to reach recipients.
You can choose between the following for suspicious emails:
- Warning Only: Emails are not blocked but are marked with explanatory warnings for the recipients
- Block: Emails are blocked and can only be released from quarantine by workspace administrators
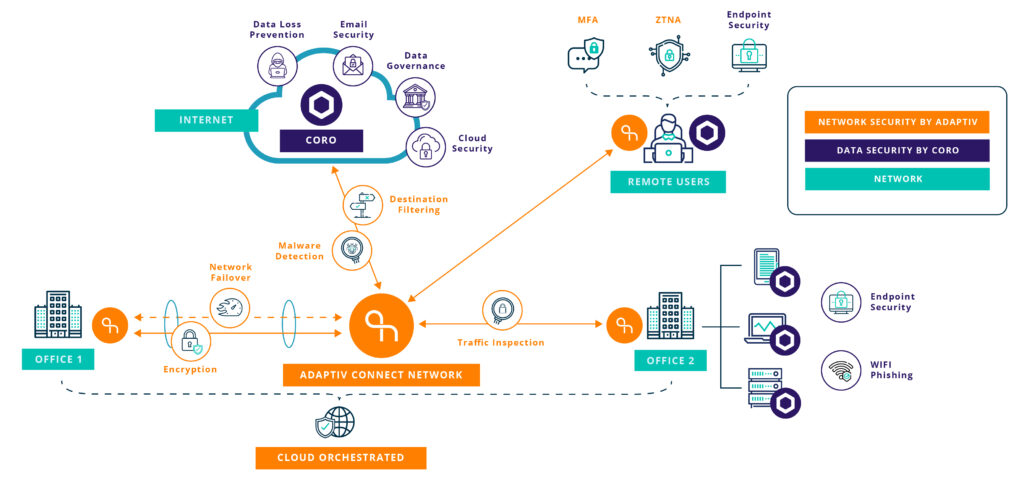
Adaptiv SD-WAN
Business Connect
Business Connect
Enterprise Connect
Enterprise Connect
My Connect
Adaptiv SASE
Network Security by Adaptiv
Data Security by CORO
Web Connect
Network Connect
Coro Essentials
Endpoint Protection
Email Protection
Bandwidth-based license
User/Device-based license
Comprehensive Network and Data Security
Adaptiv SD-WAN provides network security that fits perfectly with Coro data and enpoint security to provide comprehesive protection.
Featured Content
Frequently asked questions
Coro by Adaptiv Networks
No. Coro is a software-based soluton, a client applications is installed on user endpoints with no hardware required.
Yes. Coro can be integrated with existing cybersecurity solutions so you can choose whichever modules you need to address security gaps. Over time you can use additional Coro modules to bring all your cybersecurity into a single platform.
Yes, we do offer the option to puchase individual Coro modules. The suites offer compelling value because they are simple and you get more for your money, however we can also provide quotes for individual Coro modules on request.
Yes! Coro solutions work perfectly with ELFIQ link balancing and SD-WAN solutions. Al the Coro suites and modules are available for ELFIQ customers





